In the modern data-driven world, most organizations still don’t think about how they’re storing data for ediscovery purposes.
The consequence of this “it won’t happen to me” mentality is that they realize they don’t have the data being requested only when it’s too late.
This data preservation negligence leads Fortune 1000 companies to pay up to $30 million annually for ediscovery.
These costs could go way down if companies had considered email archiving as an integral part of their ediscovery strategy, not a separate process.
In this article, you’ll learn about:
- The ediscovery process and its parts.
- What are ESI and EDRM.
- How to handle email ediscovery requests.
- The information hidden in your email communications.
- Reducing risk with email archiving.
- How email archiving helps in ediscovery.
- Must-have email ediscovery and archiving features.
What Is Ediscovery?
All lawsuits today involve documents and information stored in electronic format.
Ediscovery is the process of identifying, collecting, and reviewing electronically stored information (ESI) during the discovery stage of a litigation process.
In the past, the discovery process was done with physical records and evidence, but today, the emphasis is put on electronic retrieval. For this to be manageable, organizations need to keep an electronic record of all information.
Federal Rules of Civil Procedure mandates the retention of electronic records, so most organizations use some kind of archiving software to meet compliance and speed up ediscovery requests.
Electronic Stored Information (ESI) Definition
Electronically Stored Information (ESI) is data that is created, received, altered, and stored in a digital format.
ESI has played a big role in legal proceedings ever since 2006, following the FRCP revision that specified which electronic information constitutes official records.
It encompasses a wide array of digital formats that can be used as court evidence or be requested.
These formats include:
- Emails
- Email attachments
- Video
- Images
- Audio files
- Text messages
- Voicemails
- Spreadsheets
- Documents
- Electronic contracts
And many more data types that contain communications or business-critical information.
ESI can be stored on any electronic device like computer hard disks, phones, or digitally on the cloud. The most reliable way to store ESI for compliance is through data archiving.
This information can then easily be retrieved when needed by using the EDRM model.
What Is the Electronic Discovery Reference Model (EDRM)?
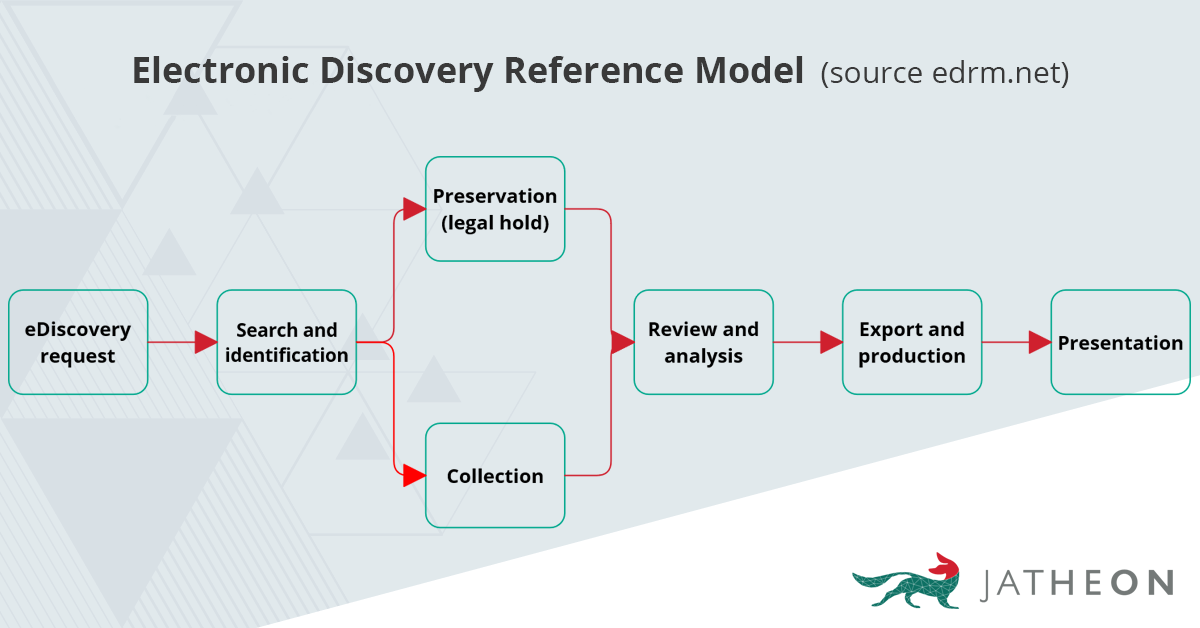
The EDRM (Electronic Discovery Reference Model) outlines the seven stages of the ediscovery process (ediscovery workflow) that an organization goes through during an ediscovery request or investigation.
EDRM is aimed at guiding ediscovery professionals on what they need to do in each step of the process for their organization to comply with ediscovery laws.
The seven stages of the EDRM process consist of:
- A trigger event — An ediscovery request or investigation for a legal case that starts off the process.
- Search and identification — An organization will work on searching for potential sources of electronically stored information (ESI) outlined by the request. This includes emails, documents, databases, and more.
- Preservation (Legal hold) — Ensures that the identified information won’t be deleted or altered.
- Collection — If the information is needed at the moment, the scope of its collection is defined including all relevant files.
- Review and analysis — Reducing the volume of information to the necessary level, deduplicating data, and reviewing the data with the legal team before the next step.
- Export and production — Converting the relevant information into a readable format (PST or PDF), redacting classified or sensitive data, preserving all of the metadata, and creating a production log.
- Presentation — Presenting the found information to the requesting party for a trial, request, or negotiation.
How to respond to an ediscovery request
Ediscovery requests can happen anytime and it’s your responsibility to respond with the requested information in a timely manner.
Once you get a request you need to respond in writing in one of three ways:
- Comply with the request — If the request is in line with the scope of the case at hand.
- Object to the request — If the requested information is irrelevant to the case. You also need to explain why you’re objecting to the request.
- Ignore the request — Not recommended as you can get sanctioned.
If you comply with the request you will need to go through it line by line and produce the requested documents or ESI.
To best respond to an ediscovery request your team needs to go through the ediscovery requirements and send the data to the requesting party in as short a period as possible.
However, this is easier said than done.
In a survey by Osterman Research, it was found that the average time it takes to respond to an ediscovery request is between 8 man-hours and 16 man-hours (1-2 full days).
The average annual ediscovery cost to companies is $5 million, 70% of which is paid to legal experts who review data.
Who is responsible for ediscovery?
IT departments are now becoming responsible for data management in many organizations because digital data is growing so fast and IT staff tend to be best equipped to deal with it.
The issue is becoming more and more complex because data storage media types have evolved and remnants of old technologies can be found mixed in with new technologies.
Importance of business communication metadata
It’s said that 75% of business-critical data resides in email, the channel which makes up the most requested data in legal cases.
ESI is very specific, not only because of its transience and intangible form, but also because of its associated metadata like the information sender, date and time received, communication threads. Very often, it’s the metadata which plays a key role as evidence.
For this reason, to preserve document metadata and to make vast numbers of corporate electronic exchanges searchable, it’s not enough to print an email or take a screenshot.
These formats are susceptible to evidence spoliation (images can be easily manipulated using editing software like Photoshop or AI tools).
Unless all metadata is captured, you’ll be losing a tremendous amount of information that could determine the outcome of your ediscovery process or litigation case.
With this in mind, how can organizations handle ediscovery requests properly?
The key is to approach it proactively and establish best practices for ediscovery:
- Create a comprehensive ediscovery policy. It should outline the procedures and responsibilities for ediscovery, and include guidelines on data retention, legal hold processes, and steps to be followed during litigation or investigations.
- Implement data management strategies. This includes categorizing data, managing data lifecycles, and ensuring data is stored in a searchable and retrievable format.
- Conduct regular employee training and raise awareness. This will ensure your employees are aware of the latest technologies, legal requirements, and company policies.
- Use advanced technology. Leverage technology like cloud-based ediscovery tools, machine learning, and AI for efficient data processing, review, and analysis.
- Ensure data security and privacy compliance. Your ediscovery practices should comply with data protection and privacy laws such as the GDPR, CCPA, or other country-specific laws. This will ensure that the way you handle sensitive data during the ediscovery process is secure and that no confidential, proprietary, or personally-identifiable information is shared by mistake.
- Implement legal hold procedures. This will help preserve relevant information when litigation is anticipated and should include suspending normal data deletion policies and notifying relevant personnel.
- Document everything. Keep reports of your ediscovery processes and document data collection, processing, and chain of custody.
Reduce Ediscovery Risks with an Email Archiving Solution
As the use of email rises, so do the risks associated with legal evidence being destroyed if relevant emails get deleted.
In 2006, the US Supreme Court’s amendments to the Federal Rules of Civil Procedure led to the creation of a new category for electronic records. This is when the law first explicitly named email, instant messages, and social media chats as likely records to be archived and requested when relevant.
This prompted businesses to start treating email and other electronic data the same as their regular data for archiving purposes and ediscovery. Simply put, corporate email is classified as a form of record.
Keeping track of every email and message sent, edited and exchanged would be impossible without technological solutions.
For email ediscovery, organizations typically use email archiving solutions to store email for long periods while having an easy way to perform ediscovery.
How Does Email Archiving Help in Ediscovery?
Email archiving solutions capture all incoming and outgoing emails from both internal and external sources.
After capturing, their copy is indexed and stored in a central repository with all of its content and metadata included.
This helps your ediscovery in five ways:
- You can be sure that the requested data isn’t deleted.
- Searching for requested data is much easier.
- All of the information needed for the case is stored.
- There’s no way of tampering with evidence.
- The data can be exported in a readable format.
This means that when you receive an email ediscovery request, you’ll already have access to a searchable archive that contains not only the entirety of your business records but also the metadata for all those records.
However the information is hard to find, archives provide a much easier and cost-effective way of searching for data unlike hiring external help for finding it.
To ensure your readiness for ediscovery, your archive needs to be equipped with five crucial features.
5 Must-Have Email Ediscovery Features
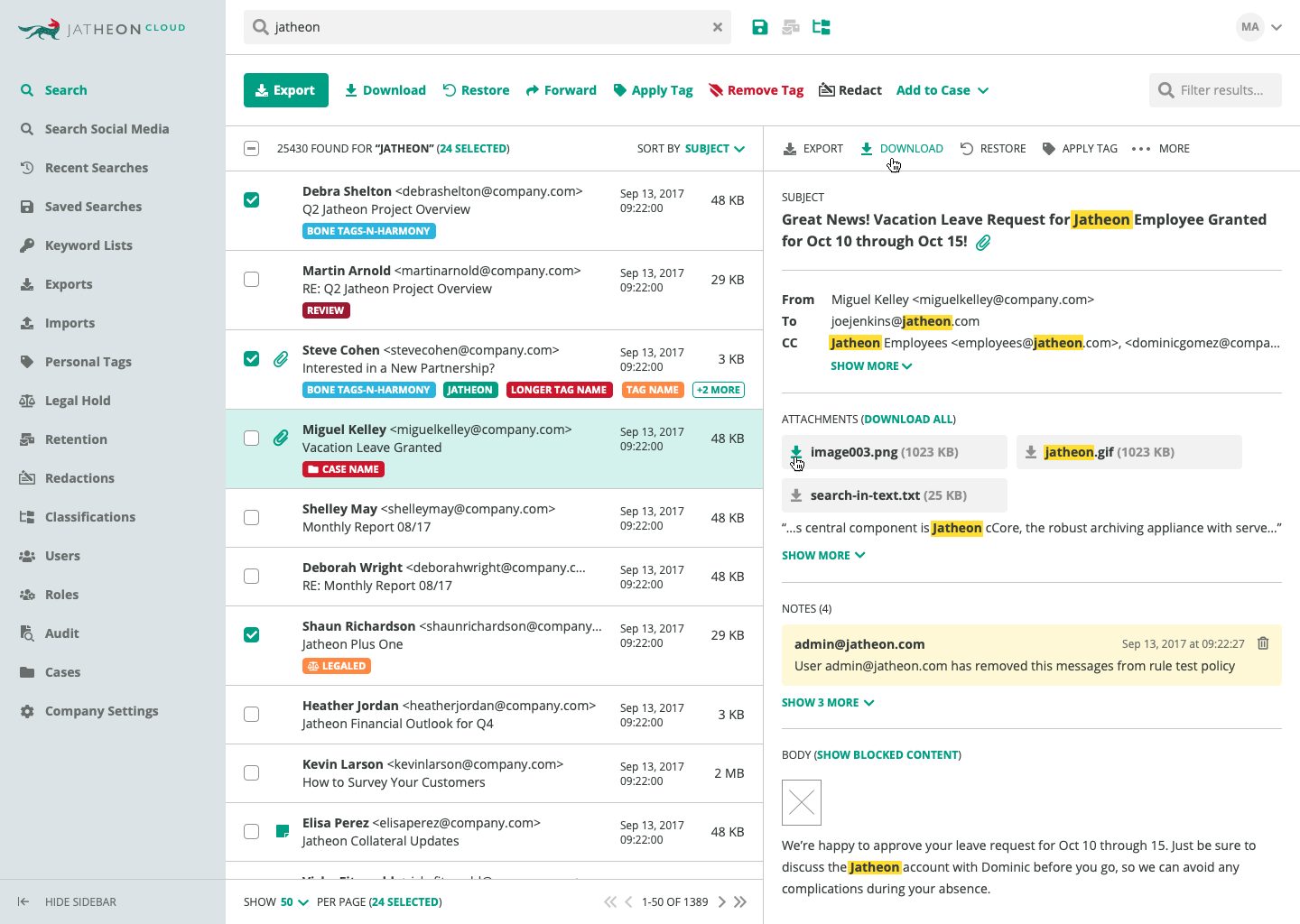
1. Advanced Search
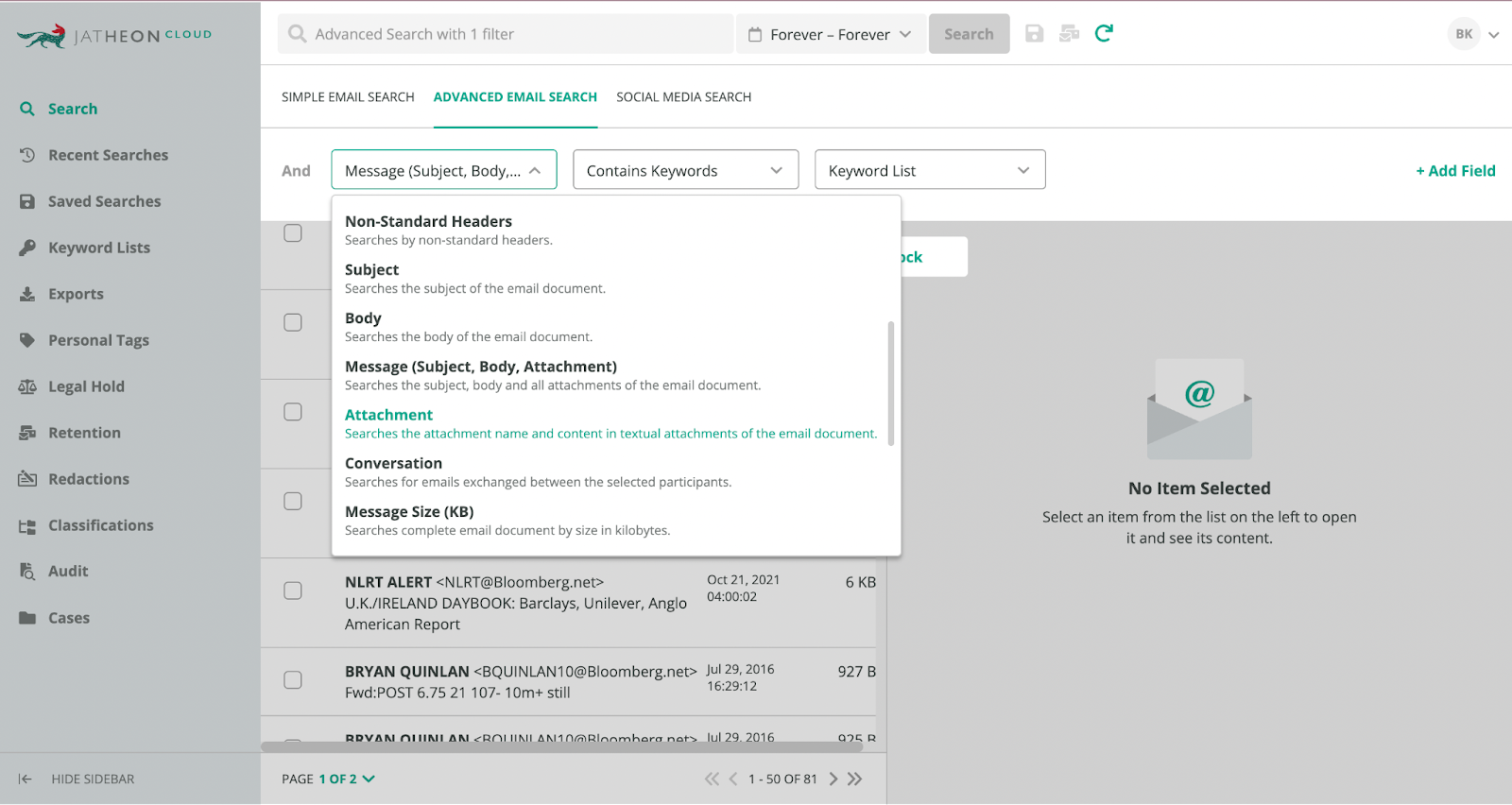
To even be taken into consideration, any email ediscovery and archiving solution must have advanced search capabilities.
You can’t present email evidence if you can’t find it or if you’re unsure that you located everything that could be relevant.
The solution you choose should be able to perform:
- Boolean search — Combine keywords with AND, OR, and NOT operators.
- Wildcard and proximity operators — Search the archive with partial terms.
- Fuzzy searches — Accommodate your search for spelling errors.
- Keyword search — Look for specific terms with a dataset.
These search options should search through subject lines, email content, senders, recipients etc. and give you an easy way to find what you need.
For instance, Jatheon allows you to combine these search options and retrieve data with pinpoint accuracy.
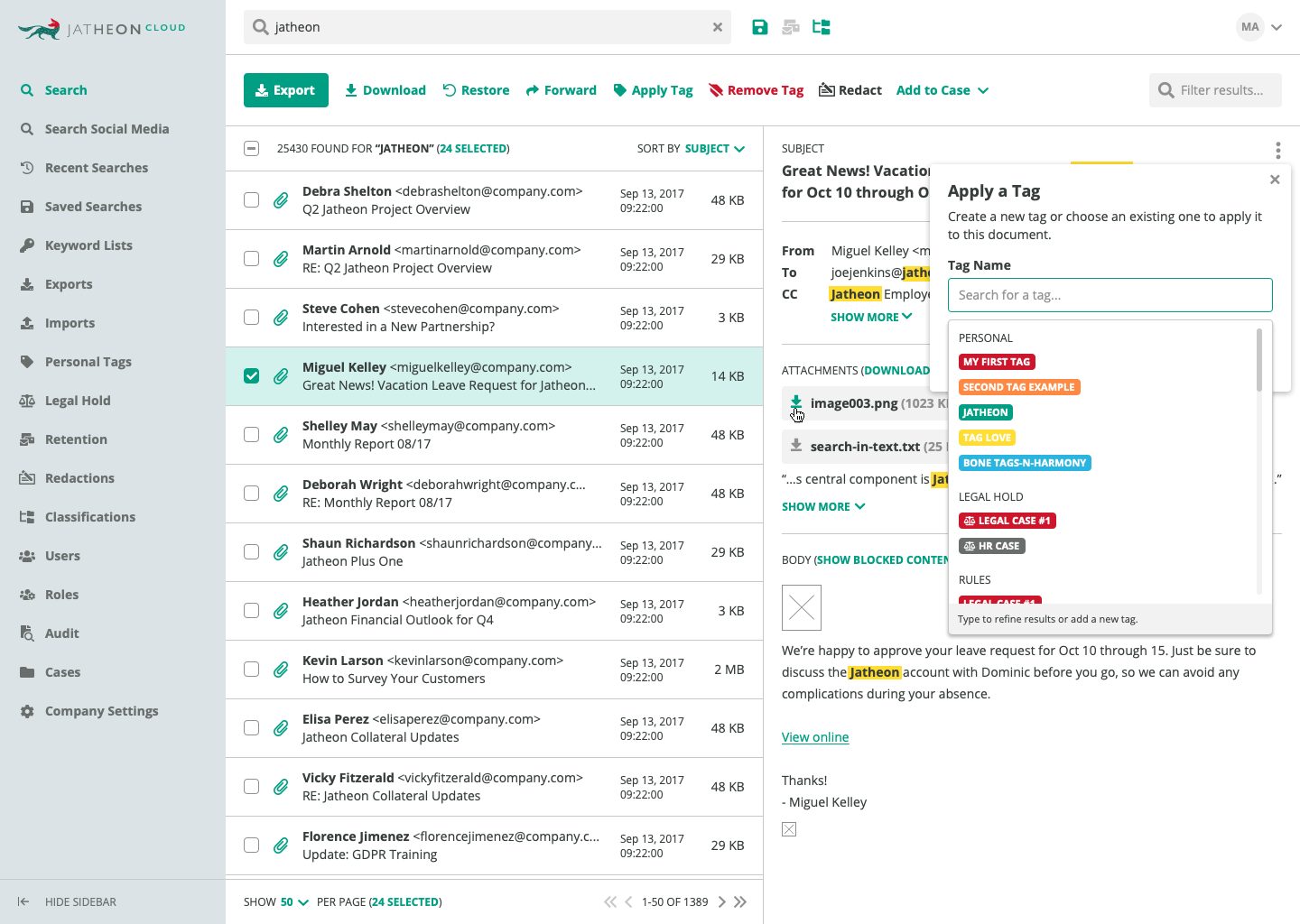
2. Legal Hold
When organizations anticipate litigation, it’s important to preserve the potential digital evidence and protect it from tampering or deletion.
Email archives are built to prohibit unauthorized deletion and tampering with data, but certain emails that contain information relevant to your current case might be scheduled for automatic deletion as per your email retention policy.
Locating those emails in your archive and applying a legal hold (typically by using tags) will supersede the automatic deletion and retain the emails in the archive for as long as you need them.
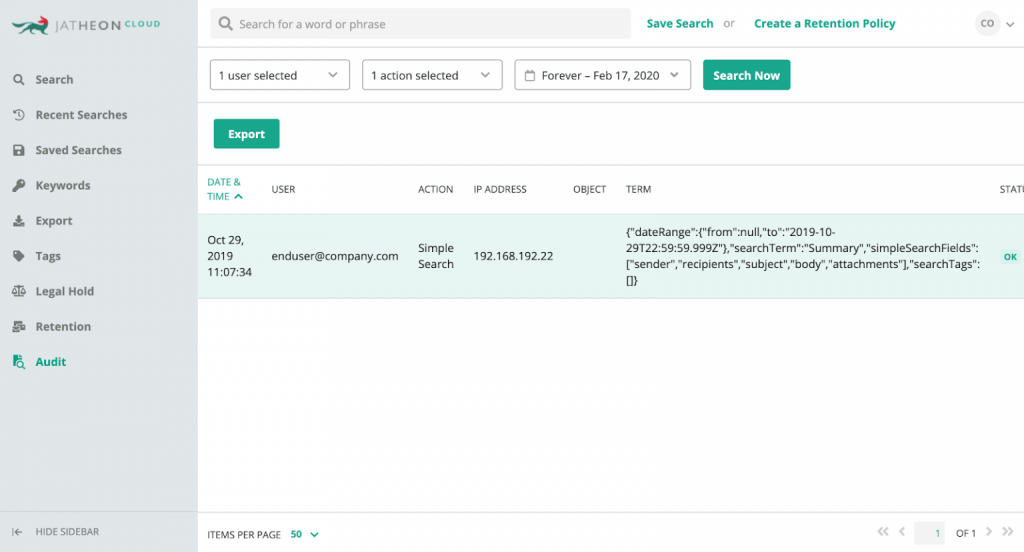
3. Audit Trail
For legal teams, it’s essential to prove that a particular email’s integrity is intact, that is, that the evidence hasn’t been fabricated or tampered with.
An email archiving solution helps you prove your email integrity because they are built to archive everything in a WORM (Write once read many) format and prevent edits and deletion.
To amplify the security, some solutions have a built-in audit trail feature that allows compliance officers to monitor user activity in the archive.
This can tell them if an employee attempted to search for a particular email, delete it, or attempt to tamper with it which can help you in a legal case.
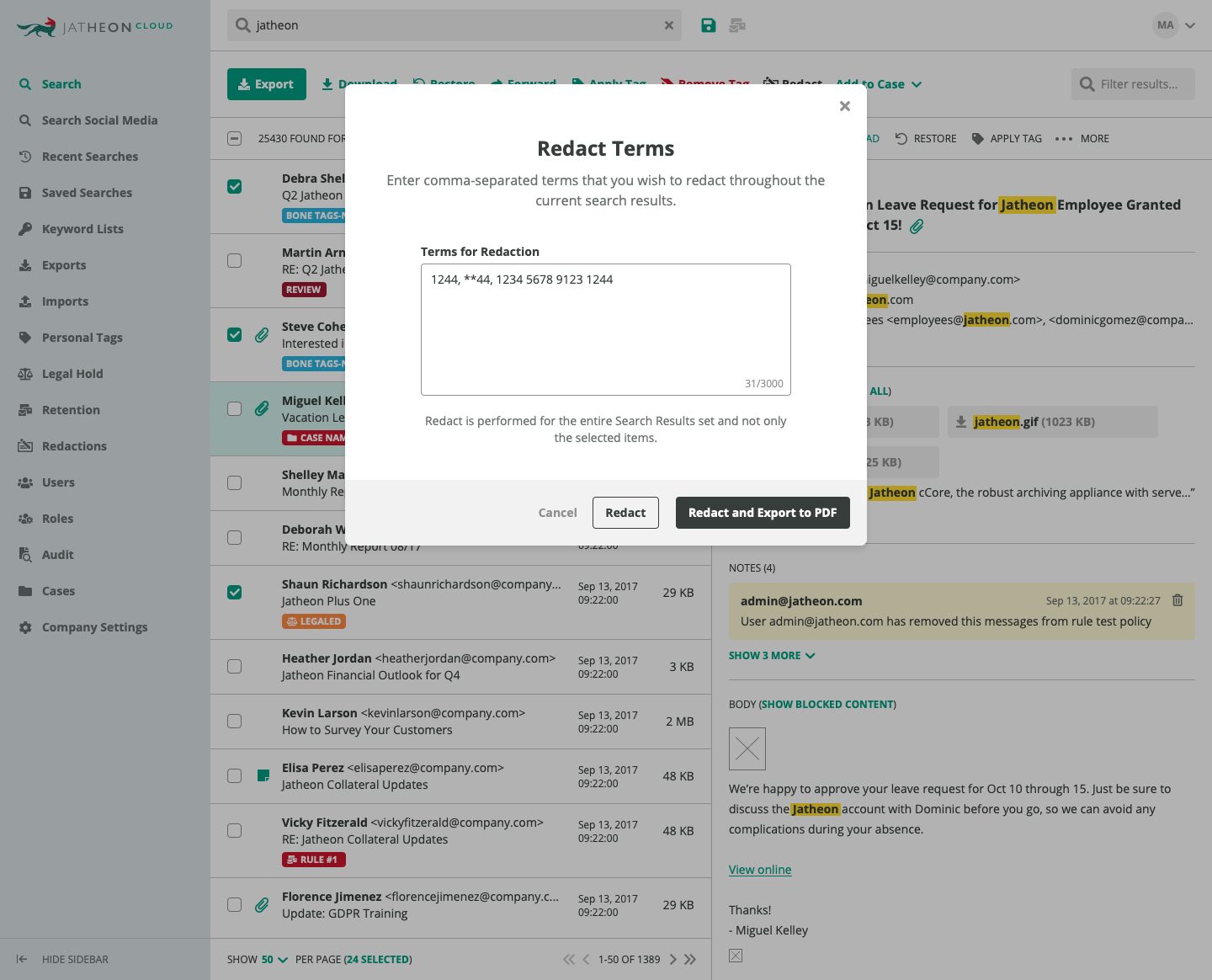
4. Redaction
The redaction feature allows authorized users to conceal personally identifiable and sensitive information (PII) directly in the email archiving software.
Some of the information that’s typically redacted includes SSN, ethnicity details, credit card info, medical history, etc.
Or if the case requires it, the archive user can redact any type of data automatically on multiple emails saving time and manual work.
The integrated redaction feature helps to shorten ediscovery request response times while staying compliant with data privacy laws and also prevents the security issues associated with sending sensitive data to a third party.
5. Export
Finally, finding and reviewing the data for ediscovery means nothing if you can’t export it securely and efficiently.
The export feature in the email ediscovery software should be able to handle large volumes of data and support various file formats like PST, EML, and PDF.
Conclusion
Email is the most dominant type of electronic communication channel and all of its content can be used as evidence in litigation.
However, many businesses struggled with ediscovery and requests due to not having optimal ways to store and search through their email data.
Email ediscovery solutions come to the rescue as a way to easily store email data as evidence without a way to get tampered with.
Solve all of your email archiving and ediscovery needs with Jatheon’s cloud archiving solution built for businesses of all sizes. Stay compliant, speed up your ediscovery, and retain all of your business data in one easy-to-use solution.
Read Next:Legal Hold Explained – The Critical Part of Email Archiving Ediscovery Software Comparison – Best Ediscovery Solutions for This Year |